Retailers have the third-highest rate of data breaches. The average cost of a breach in retail is over $3 million. Research confirms over 80% of breaches are caused by human error. As many as 60% of consumers avoid a retailer after a breach, illustrating the risk to brand reputation and financial performance beyond regulatory scrutiny and fines. Under GDPR in Europe, failure to report a breach can result in fines of up to $8.7 million or 2% of turnover. Employee can be reluctant admit mistakes. Retailers train employees and use frameworks to secure vendors and suppliers, but staff turnover is high. Technology-based solutions are increasingly common.

People and technology essential to protect data in retail
Data security is critical in durables retail. Companies deploy a combination of people and technology based efforts to mitigate high risks
People: Social & Governance impacts
Consumer durables retail
AT A GLANCE
Retailers are bombarded by cyberattacks that compromise personal and financial data.
Companies increasingly rely on a reputation for securely processing customer transactions, which is vital to maintaining or gaining market share.
High turnover employees can be a vulnerability. Companies are utilizing an array of methods to increase data security.
Multi-level frameworks
Companies align with domestic and international legislation including Europe’s GDPR, which influences global standards but also ISO 27001, ISO 27701, PCI DSS, and industry-specific regulations. Compliance and initiatives are disclosed in line with GRI/SASB standards and reveal multi-level frameworks like the committees and working groups utilised by JD and Alibaba. The latter has a Personal Information Protection Officer (PIPO), reporting directly to the president of each business line.
Third parties and vendors
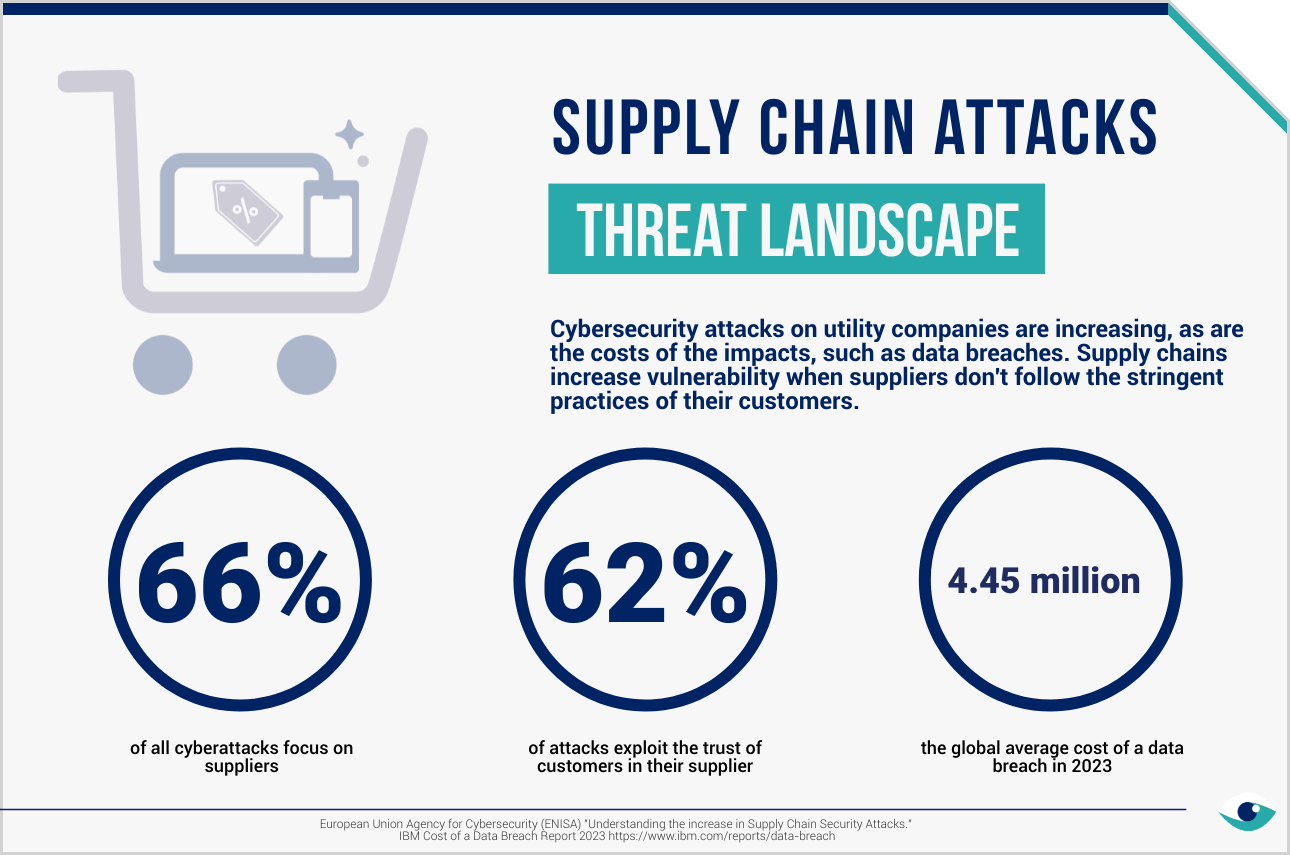
Suppliers and vendors can be vulnerable areas targeted by cyber attackers and pose the same level of risk to retailers as direct attacks. Hence, cybersecurity policy and practise extend through the value chain. Lowes vendors are required to uphold their commitment to data security and privacy by adhering to the same requirements, including the National Institute of Standards (NIST) framework and its Vendor Code of Conduct.
Cybersecurity training
Attacks to obtain personal and financial data include credential phishing, which accounts for 30% of attacks, and malware, which accounts for 21%. These attacks arrive in employee inboxes and on devices. Failure to recognise cyber risk and act exacerbates risk. Extensive data security training is normal. Home Depot, for instance, trains annually with additional role-based activities. Training impact can be diluted by high turnover in retail and employee fear of admitting mistakes.

Future solutions
Leading retailers combine people-based approaches with advanced technologies to combat just as complex cyber risks. Alibaba, for example, replaces consumer phone numbers with virtual numbers where subscribed to avoid phone fraud and safeguard consumers. It has launched a marketing privacy platform Secure Data Hub (SDH), for compliant use of private data in advertising and has released over 10 institutional norms for data security and privacy protection.
FURTHER READING
- General Data Protection Regulation (GDPR)
- “Psychology of Human Error” Could Help Businesses Prevent Security Breaches (CISO MAG)
- Cost of a Data Breach: Retail Costs, Risks and More To Know (Security Intelligence)
